| | | | | | | Presented By Wiz | | | | Axios Codebook | | By Sam Sabin · Dec 19, 2023 | | Happy Tuesday! Welcome back to Codebook. - 🎊 Today's edition is the last of 2023. Thanks so much for supporting Codebook, and see y'all in the new year!
- 📬 Have thoughts, feedback or scoops to share to help us kick off 2024? codebook@axios.com.
🚨 Situational awareness: A ransomware gang has leaked 1.67 terabytes of data stolen during a hack of Sony's Insomniac Games — including apparent licensing agreements, budgets and details about the upcoming Wolverine game release. Today's newsletter is 1,490 words, a 5.5-minute read. | | | | | | 1 big thing: The year security executives' jobs changed |  | | | Illustration: Aïda Amer/Axios | | | | New regulations and emerging technologies redefined the role of security executives this year. Why it matters: Chief information security officers now need a new set of skills to be successful, executives told Axios. The big picture: Security executives are now facing an unparalleled number of challenges as artificial intelligence gains popularity and helps malicious hackers create even more believable lures for social engineering scams. What they're saying: "It's a very tricky balancing act, and we're all under immense pressure to get it right," Kayla Williams, CISO at security analytics company Devo, told Axios. Between the lines: New AI tools, regulations and hacking tactics are forcing security executives to change their ways — and are changing the way the rest of the C-suite interacts with security teams. - As companies continue to embed generative AI tools into their workflows, security executives are tasked with ensuring those models don't accidentally gobble up or share proprietary company information with the public.
- Hackers have also fine-tuned their social engineering skills to trick employees into sharing their passwords — forcing security executives to rethink internal cybersecurity programs.
- And new Securities and Exchange Commission regulations, which just went into effect this month, put increasing pressure on security executives to perfect their internal cybersecurity programs or face legal consequences.
Details: Each of these events means that security executives are no longer just the best security engineer at their company — they also need better communications and business skills to work effectively with other teams. - Security leaders have spent the last few years learning how to translate their highly technical workflows for nontechnical leaders and board members — but that evolution now has to pick up the pace as companies face new regulatory obligations, Geoff Belknap, CISO at LinkedIn, told Axios.
- "The executive staff and the board are increasingly looking for the CISOs to bring a strong point of view to the table and help leaders understand the level of cyber risk and make informed decisions on how to manage that risk," Brian Spanswick, CISO and CIO at tech company Cohesity, told Axios.
Meanwhile, companies' continued AI integration also means security executives are being pulled into product development conversations earlier, Belknap added. - "For a long time, the status quo was to bring infosec in at the very end of the product or platform development process and expect them to wave a wand and make it secure," he said.
- "Now, development teams are increasingly seeing their infosec colleagues as partners rather than obstacles, and that's for everyone's benefit."
Zoom out: Security leaders have also been faced with defining how their organizations can safely deploy AI while actively learning what it's capable of. - "This meant that security executives like myself collaborated with other members of the C-suite and the board more than ever before to build these practices and directly drive business outcomes," Phil Venables, CISO at Google Cloud, told Axios.
Yes, but: Heightened C-suite awareness of cybersecurity threats has made some security leaders' jobs easier — they no longer have to spend nearly as much time explaining why security should be a top priority. - "That's the perspective more people are starting to take when it comes to cyber — less talk, more action," Gary Barlet, field chief technology officer for Illumio's federal business, told Axios.
What we're watching: In 2024, the new plans security leaders have put in place to address these concerns will be tested for the first time. |     | | | | | | 2. Law enforcement goes after BlackCat ransomware | 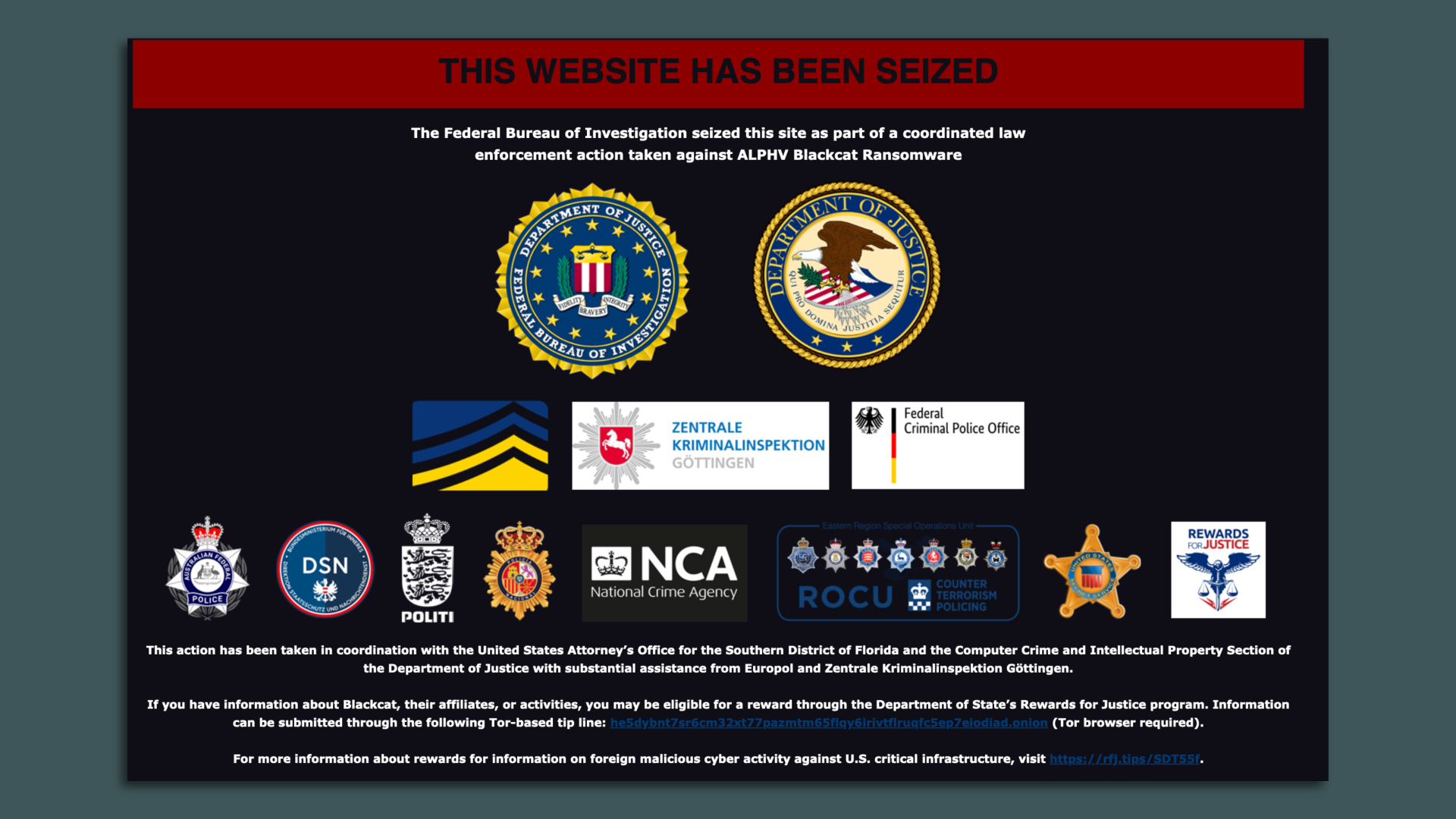 | | | Screenshot: Law enforcement seizure notice on the BlackCat ransomware gang's dark web site. | | | | Federal law enforcement officials announced Tuesday they had taken down the online infrastructure belonging to the BlackCat ransomware gang and offered victims a decryption key. Why it matters: The takedown disrupts the operations of what the Department of Justice believes is the "second most prolific ransomware-as-a-service variant" circulating around the world right now. The big picture: BlackCat, also known as ALPHV or Noberus, is estimated to have targeted more than 1,000 victims since its inception more than 18 months ago, according to the DOJ. - Federal officials also said the hacks disrupted U.S. critical infrastructure, including government facilities, emergency services, defense industrial base companies, critical manufacturing, and healthcare and public health facilities.
- Some of the gang's victims have included hospitals, data storage company Western Digital and drug manufacturer Sun Pharmaceuticals.
- BlackCat's ransomware is also believed to be linked to the hack on MGM Resorts this year.
Details: A law enforcement seizure notice is now on the BlackCat gang's dark-web leak site, per a notice seen by Axios. - The notice indicates that the FBI worked alongside a set of international law enforcement partners, including Australia and countries across Europe, to take down the site.
Meanwhile, the DOJ said the FBI had developed a decryption tool to help the gang's victims who came to law enforcement. - During the investigation, the FBI offered the tool to more than 500 victims to restore their systems after the BlackCat gang, or its affiliates, deployed file-encrypting malware.
- The FBI worked with dozens of victims in the U.S. and internationally to recover their systems, sparing victims from a total of $68 million in ransoms, per the DOJ.
Yes, but: Online infrastructure takedowns are often a short-term solution for stopping ransomware gangs from operating. |     | | | | | | 3. What to know about the new SEC cyber rules |  | | | Illustration: Allie Carl/Axios | | | | A new regulatory regime is now in effect, and public companies are still scrambling to figure out what it means for them. Why it matters: Companies have often resisted disclosing cyberattacks and other incidents until the issues are resolved, which can take weeks or months. - The new Securities and Exchange Commission rules will bring most of these attacks to the public's attention much sooner.
Driving the news: The SEC's new cyber disclosure rules went into effect this week. - Now, publicly traded companies must report cyber incidents that have a material impact on the organization within four business days via a public 8-K filing, as well as share details about the company's internal cyber program in annual 10-K reports.
The big picture: Despite the SEC passing the rules in late July, companies are still wrestling with some pretty big questions about what's expected in these disclosures and how the public will respond to them. Details: Erik Gerding, director of the SEC's division of corporation finance, attempted to answer some of those lingering questions in a blog post last week. - Gerding clarified that cyber incident disclosures do not need to provide "specific or technical" details that would make a company more vulnerable to an attack.
- The commission is solely seeking disclosures that an incident happened and information about what the likely impact of the incident appears to be, Gerding added.
- Disclosures are also only needed four days after a business determines the incident had a material impact — not four days after the incident occurred.
Meanwhile, the Department of Justice recently clarified how it plans to handle requests for reporting delays in cases that could affect national security. - Under the SEC rules, the DOJ can grant companies a delay in publicly reporting cyber incidents to the SEC when doing so would hurt national security.
- The DOJ plans to grant these exemptions in cases where hackers have targeted a system that contains sensitive government information or exploited a security vulnerability that doesn't yet have a patch, and in similar situations.
Yes, but: The true impact of the SEC's rules might not be as dramatic as some business leaders have claimed. - Many companies had already been reporting material cyber incidents in SEC filings for years — and those filings tended to provide basic information about the scope and impact of an incident.
|     | | | | | | A message from Wiz | | Keep your online business secure and boost your AWS security posture | | |  | | | | In the age of the cloud, businesses must take a new approach to protecting themselves — and their customers — against cyberattacks. What you need to know: Wiz, a cloud security platform, has released a free e-book that shares the most important principles for effective AWS security. Download it now. | | | | | | 4. Catch up quick | | @ D.C. 💻 The Cybersecurity and Infrastructure Security Agency is urging tech vendors to ditch default passwords altogether. (CyberScoop) 🗳️ Hackers linked to Russia and China targeted some election systems during the 2022 midterms but ultimately had no impact on the integrity or security of election systems, according to a new intelligence community report. (Reuters) ⛺️ Outdoor retailer L.L. Bean has become one of the biggest supporters of a tech industry-backed privacy bill in Maine. (Politico) @ Industry 💰 IBM plans to acquire Software AG's enterprise integration platforms business for 2.13 billion euros ($2.33 billion). (Reuters) @ Hackers and hacks ⚠️ The FBI estimates that more than 300 organizations have faced attacks from the Play ransomware gang, per a new advisory. (CISA) 🔍 MongoDB, a widely used database program, is investigating a security incident that exposed customer information. (BleepingComputer) 🏠 Mortgage and loan giant Mr. Cooper confirmed that hackers stole the personal information of 14.6 million customers in a recent cyberattack. (TechCrunch) |     | | | | | | 5. 1 fun thing |  | | | Screenshot: @uuallan/X | | | | I'm pretty excited to see where this newly announced cybersecurity comic book anthology goes! - 💥 Submit your ideas here.
|     | | | | | | A message from Wiz | | Protect your AWS business — and customers — against cyberattacks | | |  | | | | Businesses must keep up with the speed of the cloud. AWS Security Foundations for Dummies walks through important security principles, including how to: - Monitor your AWS security posture.
- Protect AWS data in transit and at rest.
- Respond to and fix security incidents.
- And more.
Get the e-book. | | | | 🥳 See y'all in 2024! Thanks to Scott Rosenberg and Megan Morrone for editing and Khalid Adad for copy editing this newsletter. If you like Axios Codebook, spread the word. |  | Your essential communications — to staff, clients and other stakeholders — can have the same style. Axios HQ, a powerful platform, will help you do it. | | | | | | Axios thanks our partners for supporting our newsletters.
Sponsorship has no influence on editorial content. Axios, 3100 Clarendon Blvd, Arlington VA 22201 | | | You received this email because you signed up for newsletters from Axios.
To stop receiving this newsletter, unsubscribe or manage your email preferences. | | | Was this email forwarded to you?
Sign up now to get Axios in your inbox. | | | | Follow Axios on social media:    | | | | | |








No comments:
Post a Comment